Almost three years ago, I presented at the Australian Network Operators’ Group annual event (AusNOG 2017) on the local community’s ‘modest’ adoption rate of Resource Public Key Infrastructure (RPKI) — the specialized public key infrastructure framework designed to secure the Internet’s routing infrastructure.
At the time, 1.2% of Australia’s 16,794 prefixes had valid Route Origin Authorizations (ROAs). ROAs are digitally signed objects that provide a means of verifying that an IP address block holder has authorized an Autonomous System (AS) to originate routes to one or more prefixes within the address block. Correctly creating and signing them so they appear valid is the first step in implementing RPKI.
Read: Community comes together to make deploying RPKI easier
Admittedly, RPKI was relatively new back then, with ‘major’ networks still another two years away from filtering invalid routes. Indeed, this figure may still be representative of the global adoption rate if not for the efforts of AT&T (AS7018), Telia Carrier (AS1299), and NTT Communications (AS2914) to start dropping invalid ROAs.
The effort by these three and others has undoubtedly resulted in thousands of downstream operators, including those in Australia, to make sure their ROAs are showing as valid or risk service disruption. But to what effect?
Well, in Australia and New Zealand, it certainly seems to be ‘quite a bit’ going by the recent figures I presented at the Networking From Home Oceania event earlier this month.
The number of valid ROAs is on the rise
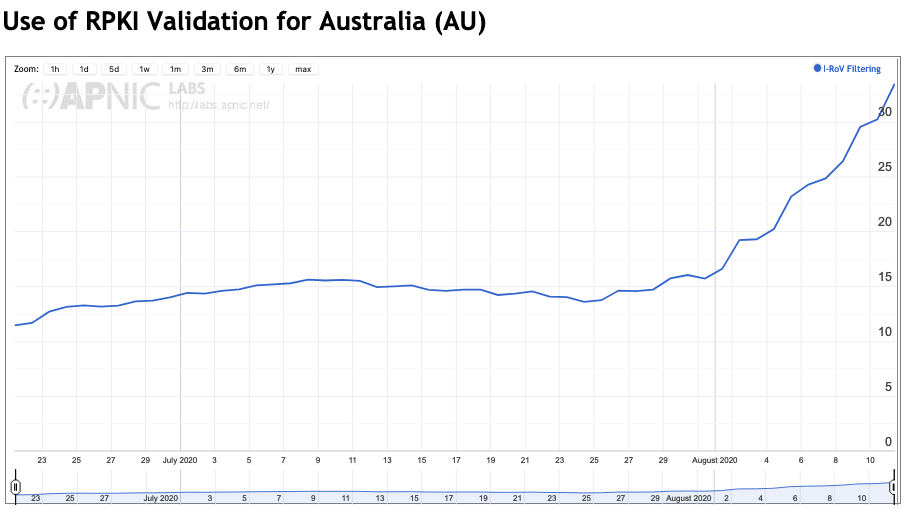
In the past three years, the number of valid prefixes in Australia has increased to 15%.
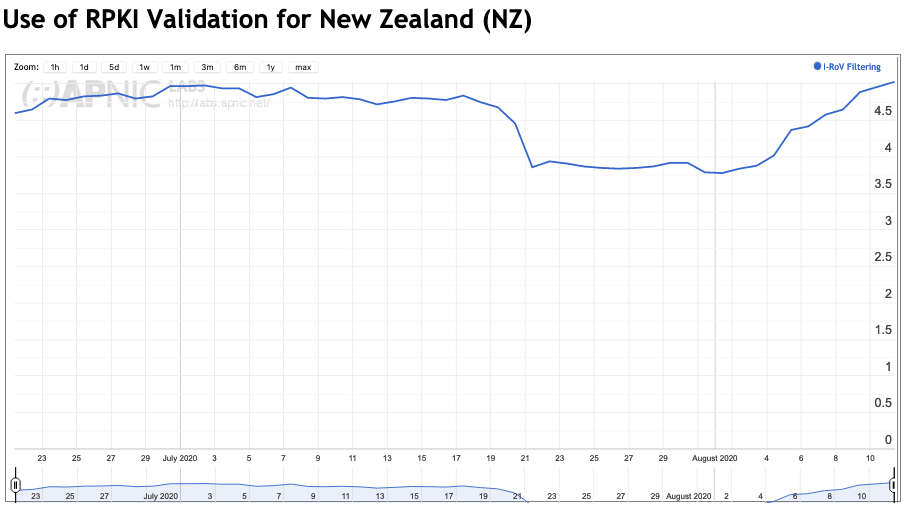
Similarly, New Zealand’s number of prefixes has also risen from 9% to 19% over the same time.
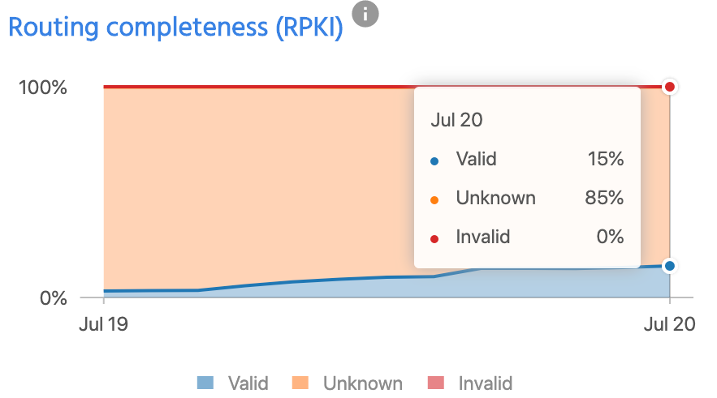
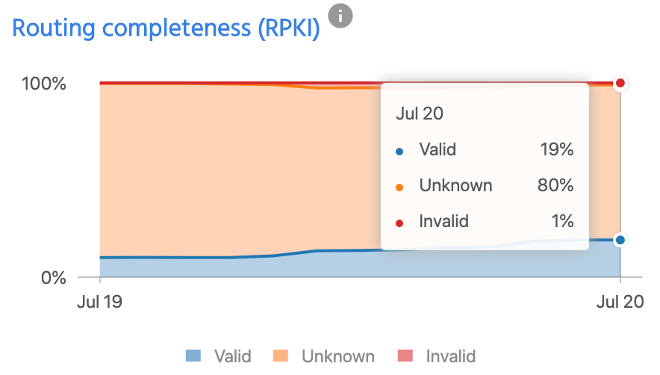
The above two embeds from RIPEstat show the Validated ROA Payloads (VRPs) coming from the RIPE NCC RPKI Validator (v3), for Australia and New Zealand.
While it seems Australia’s neighbour is leading this two-horse race, it’s worth noting the size of each economy — there are more than four times more ASNs registered in Australia than New Zealand — as well as the providers that have correctly signed their ROAs.
In terms of the latter, in Australia, incumbent Telstra (AS1221) has been a leading proponent, not only correctly signing their ROAs but also now starting to validate and filter for invalid ROAs. Other major providers leading the way include Aussie Broadband (AS4764) and Superloop (AS38195).
In New Zealand, three of its largest carriers, Spark (AS4648), Vodafone NZ (AS4768) and Snap Internet (AS23655) have 99% or 100% of unknown ROAs. One can only assume that they are still in their ‘testing’ stages but at least they aren’t contributing to the rise of invalid ROAs that still plague the APNIC region.
Signing is one thing, validating is another
We also need to consider validation in order to understand and assess the routing security efforts of these economies in the context of RPKI.
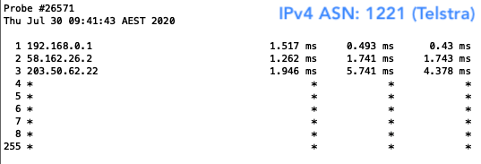
As noted, Telstra (AS1221) has recently started to implement Route Origin Validation (ROV); which, as you could imagine for a Tier 1, has had a significant effect on Australia’s overall validation figure.
In New Zealand, this figure is a lot less; no great surprise, because if you don’t have valid routes then you won’t be practising ROV.
Wanting to validate these figures for myself, I conducted an experiment in Sydney with the help of RIPE NCC’s Atlas probes. Using my personal IPv4 prefix (signed and valid, of course) and my BGP router (FRR 7.3) hosted at Vultr (AS20473), also based in Sydney, I ran trace routes to around 160 networks (using Atlas probes) across Australia and New Zealand to see if I could reach them, and, ultimately, uncover/validate if they were practising ROV.
First, I tried to reach the IPv4 address from AU and NZ probes with a valid ROA and the results were successful; afterwards I deleted the ROA and tested it again.
Warning: don’t do this on your work network.
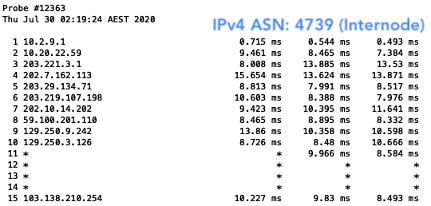
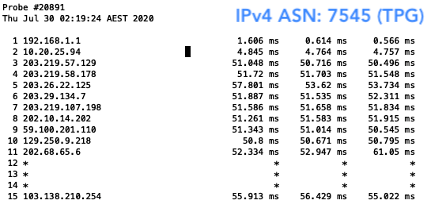
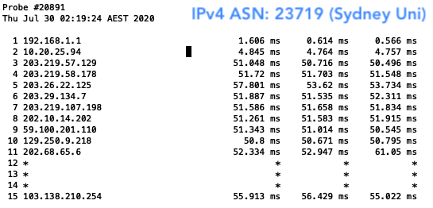
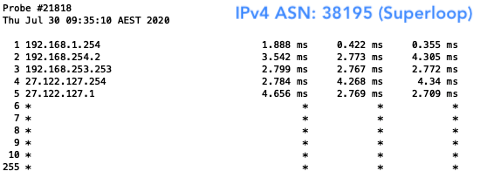
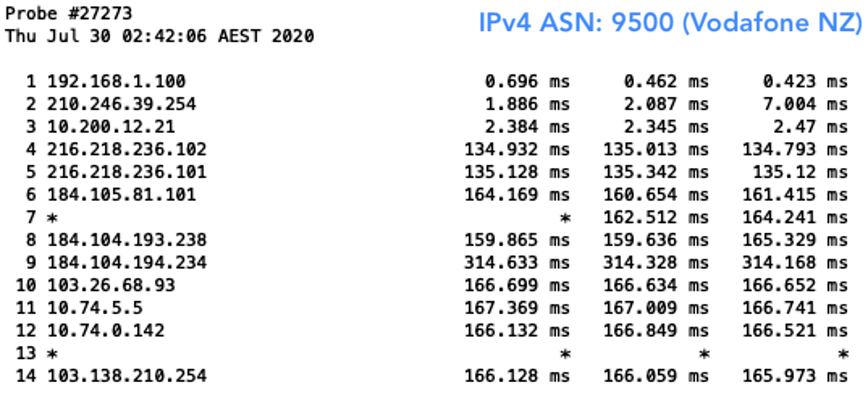
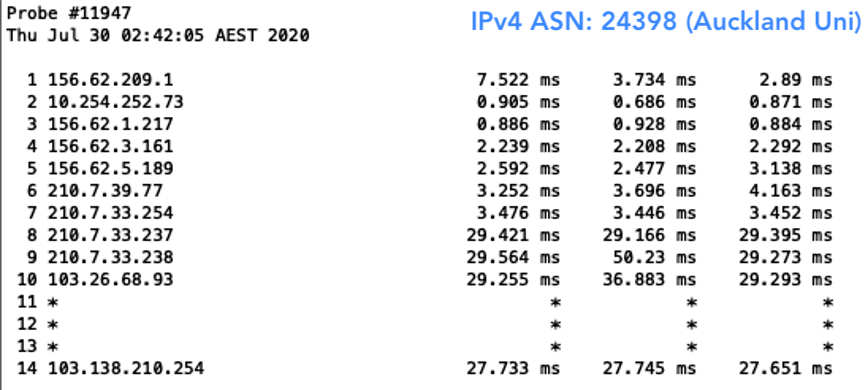
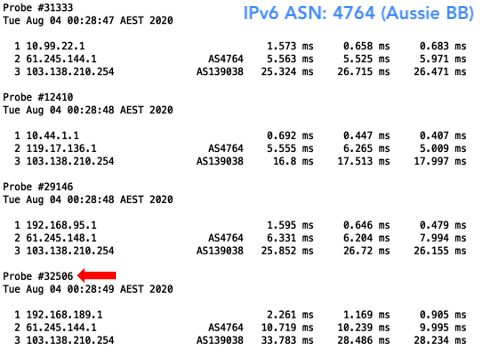
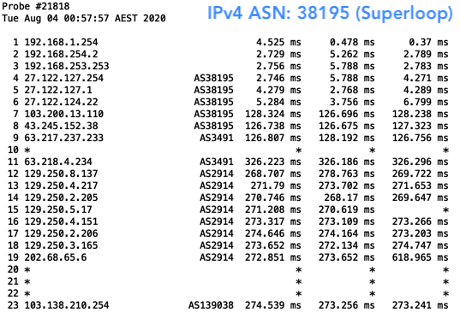
The result? Well, I was able to, of course, reach all networks with my valid prefix. But when I deleted my ROA, I was only able to reach those that were not filtering for ROAs. This meant I wasn’t able to reach Aussie Broadband (AS4764), Superloop (AS38195) and Telstra (AS1221) in Australia. As for New Zealand, I could still reach them all because none of the networks hosting the probes had deployed ROV.
Figure 5 — Australian networks that were reachable without a ROA.
Figure 6 — Australian networks that weren’t reachable without a ROA.
Figure 7 — New Zealand networks that were reachable without a ROA.
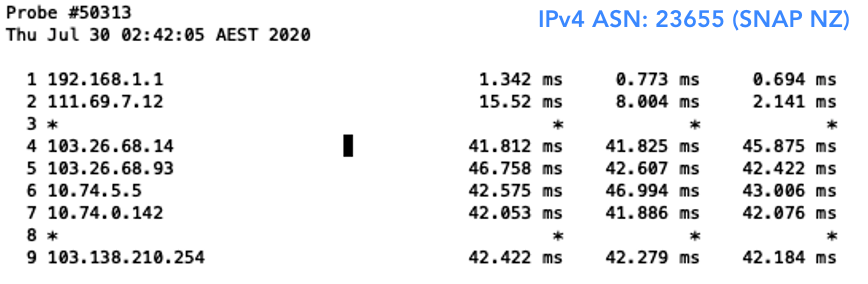
It’s worth mentioning that I did get variable results with Aussie Broadband and Superloop sometimes accepting my invalid prefixes. Digging into these traces I noticed this was due to them taking variable routes, which I’m guessing they don’t have filtering set up for yet.
Figure 8 — The above two trace routes to Aussie Broadband and Superloop were examples of how they were sometime reachable without a ROA.
Perhaps the most surprising and reassuring result from my testing, though, was Vultr emailing me saying I had an invalid ROA and if I didn’t fix it soon, they would stop advertising it.
As an RPKI and MANRS advocate this filled me with great optimism that the message is starting to ‘filter through’, and organizations are taking it upon themselves to educate and nudge their clients about the importance of routing security. As we’ve all learnt, our networks are only as secure as our peers.
Aftab Siddiqui is a Senior Manager, Internet Technology — Asia-Pacific for the Internet Society.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.